Cybersecurity Program Basics
Starting to plan out a Cybersecurity program for your company can be a challenging task, but in many ways the steps to take have more benefits than just increased security.
Introduction
Cybersecurity programs are categorized into people, technology and process. People refer to the employees, contractors, and other individuals who work for the organization and contribute to its success. Technology refers to the tools and systems used by the organization to carry out its operations, such as computers, software, and other equipment. Process refers to the specific methods and procedures used by the organization to accomplish its goals and objectives.
In the context of cyber security, people, technology, and process are all important factors that can affect the effectiveness of an organization's security measures. People, for example, play a critical role in protecting an organization's systems and data. This can involve implementing strong password policies, regularly updating software and security systems, and providing employee training on cyber security best practices.
Technology, on the other hand, is the foundation of an organization's cyber security program. This can include things like firewalls, intrusion detection systems, and encryption tools, which are all designed to protect against potential cyber threats.
Finally, process refers to the specific procedures and protocols that an organization has in place to respond to cyber security incidents. This can include things like establishing protocols for responding to data breaches, as well as regularly conducting risk assessments to identify and address potential vulnerabilities.
Process
Defining Risk & Responsibility
First, conduct a security audit to identify potential vulnerabilities and weaknesses in the company's existing IT infrastructure and systems. This could involve analyzing the network architecture, performing penetration testing, and reviewing the security policies and procedures that are in place. If no Cyber policies are in place a new basic policy should be created. This policy should include verbiage around implementing strong password policies, regularly updating software and security systems, and providing employee training on cyber security best practices.
Additionally, a strong cybersecurity program should inventory and assess the companies' "crown jewels". Crown jewels refer to an organization's most valuable and sensitive assets. These can include things like confidential financial information, sensitive customer data, or proprietary intellectual property. Protecting these assets is of the utmost importance, as they are the key to an organization's success and can be severely impacted if they are compromised by a cyber attack.
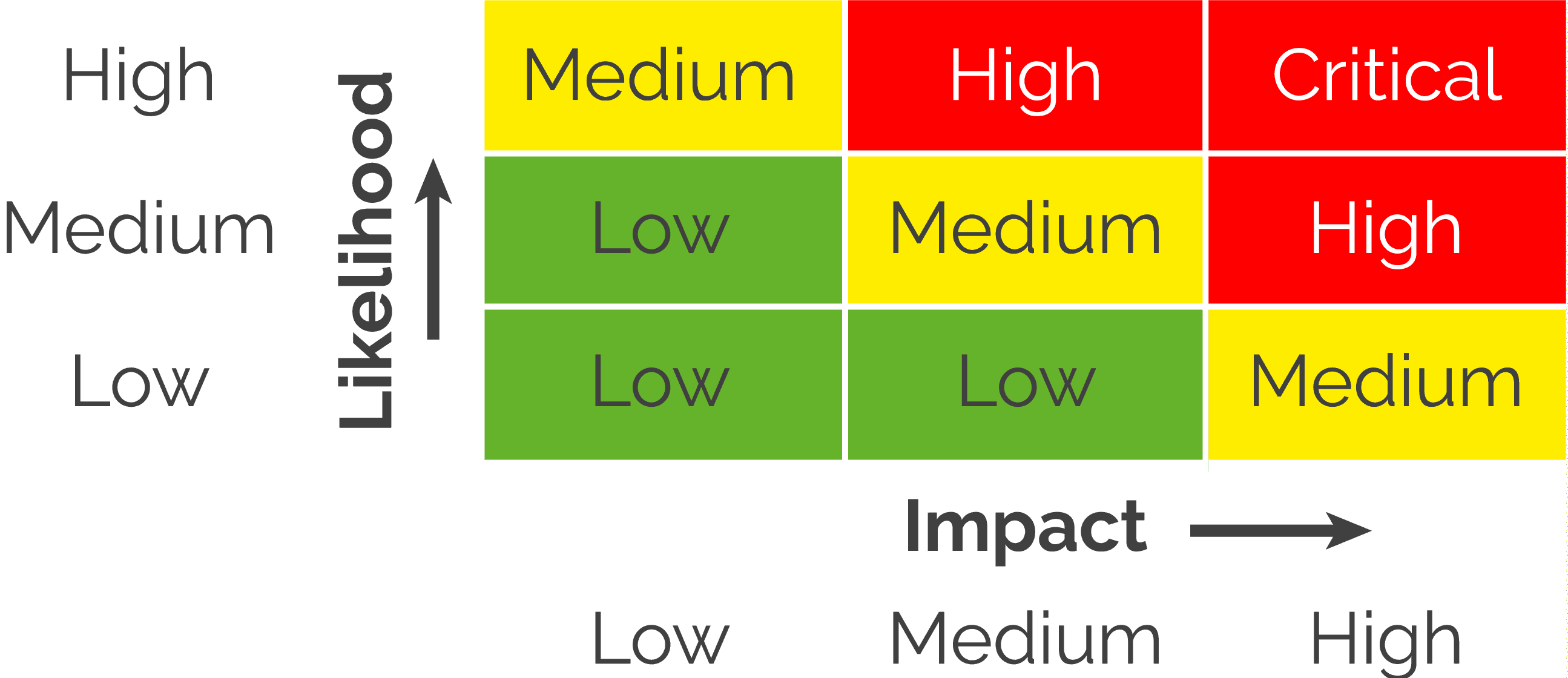
The Risk Matrix
Crown jewels and all other assets should be added to a risk matrix. A risk matrix is a tool used to identify and assess the risks associated with a particular activity, situation or impact on an asset. To create a risk matrix, you first need to identify the potential risks associated with your companies activities. This can involve conducting a thorough risk assessment to identify the likelihood and potential impact of various cyber threats. Once the risks have been identified, you can use a grid or table to plot them on a matrix according to their likelihood and potential impact. This will allow you to visually represent the risks and prioritize them based on their overall level of severity.
Furthermore, a RACI (Responsible, Accountable, Consulted, Informed) chart is another tool that can be used to help manage the risks associated with a cyber security program. A RACI chart is a visual representation of the roles and responsibilities of different individuals or teams in relation to a specific activity or project. It is commonly used to clarify who is responsible for each task or decision, as well as who needs to be consulted or informed along the way.
To create a RACI chart for a cyber security program, you first need to identify the key tasks or activities involved in implementing and maintaining the program. Next, you need to assign specific roles to each task or activity, such as "responsible" for performing the task, "accountable" for ensuring it is completed, "consulted" for providing input or advice, and "informed" for being kept up to date on progress. By clearly defining roles and responsibilities, a RACI chart can help ensure that everyone involved in the cyber security program knows their part in protecting the organization from potential threats.
Incident Response
An incident response plan is a document that outlines the steps an organization will take in response to a cyber security incident. It is designed to help the organization quickly and effectively respond to a security breach, data loss, or other cyber security incident in order to minimize the potential impact and prevent further damage.
An incident response plan typically includes several key elements. First, it will outline the specific steps that need to be taken in the event of an incident, such as who needs to be notified, what systems need to be shut down, and how to contain the damage. It will also include information on how to conduct a post-incident analysis to determine the cause of the incident and how to prevent it from happening again.
In addition, an incident response plan will typically include a list of contact information for key personnel who will be responsible for managing the response to the incident. This can include the incident response team, IT staff, legal team, and any other individuals who may need to be involved in the response.
The incident response plan should incorporate the previously defined risk matrix and RACI.
Technology
One way that technology can be used in a cyber security program is through the implementation of firewalls and intrusion detection systems. Firewalls are designed to prevent unauthorized access to an organization's systems and networks, while intrusion detection systems monitor network traffic for suspicious activity and alert administrators if they detect a potential threat.
Another way that technology can be used in a cyber security program is through the use of encryption tools. Encryption is the process of encoding data so that it can only be accessed by authorized individuals. By encrypting sensitive data, organizations can help protect it from being accessed by unauthorized parties.
In addition, technology can also be used to provide employee training on cyber security best practices. This can include things like online training modules, videos, and other educational materials that can help employees understand how to protect the organization's systems and data from potential threats.
Regularly monitor and review the effectiveness of the security measures that are in place, and make changes as needed to ensure that the company's systems and data are adequately protected. This could involve conducting periodic security audits and testing, as well as staying up-to-date with the latest security threats and best practices.
People
People play a critical role in a cyber security program. While technology can provide a number of important security measures, it is ultimately the people who are responsible for implementing and following these measures in order to protect an organization's systems and data from potential cyber threats.
Train employees on security best practices, such as the importance of strong passwords, avoiding phishing scams, and the proper handling of sensitive information. This will help to reduce the risk of human error and ensure that all employees are aware of their role in maintaining the security of the company's systems.
In addition, people can also be used to monitor for potential cyber security threats. This can involve establishing a system for reporting potential incidents, as well as regularly conducting risk assessments to identify and address potential vulnerabilities.
Conclusion
In conclusion, there are several key factors that are important for a successful cyber security program. These include technology, people, and process.
Technology is the foundation of any cyber security program, providing the tools and systems necessary to protect against potential threats. This can include things like firewalls, intrusion detection systems, and encryption tools.
People are also critical to the success of a cyber security program. This includes not only the employees who are responsible for implementing and following security measures, but also the individuals who are responsible for managing and overseeing the program.
Finally, process is essential for ensuring that a cyber security program is effective and efficient. This can involve things like conducting regular risk assessments, establishing protocols for responding to incidents, and regularly training employees on cyber security best practices.
Overall, by combining technology, people, and process, organizations can effectively protect themselves from potential cyber threats and ensure the security of their systems and data.
