Palo Alto XSOAR + GPT-3
In this post, I will be discussing how security automation can benefit from the advanced language understanding capabilities of GPT-3. By integrating GPT-3 into XSOAR, security teams can leverage the power of natural language processing to improve the efficiency and effectiveness of their incident response processes. I will be walking through the steps for setting up the integration and providing examples of how GPT-3 can be used in security automation workflows. I hope that this post will provide valuable insights for anyone looking to incorporate GPT-3 into their security operations.
Find my OpenAI GPT-3 content pack here: https://github.com/Frohrer/xsoar/tree/main/OpenAI_GPT-3_Contribution_Pack
Download and install the content pack above into XSOAR. Please understand this integration is provided as-is and will contain bugs.
Create a new instance of the integration with your OpenAi API credentials.
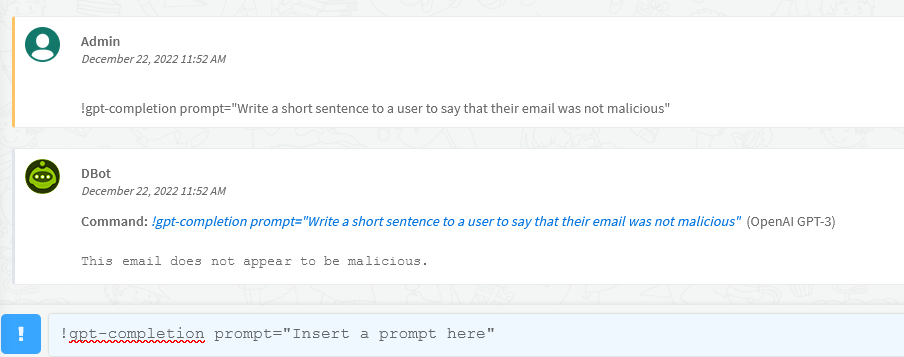
The GPT integration will respond to the generic commands "!gpt-completion" and "!gpt-edit" with the completion and the edit API respectively.
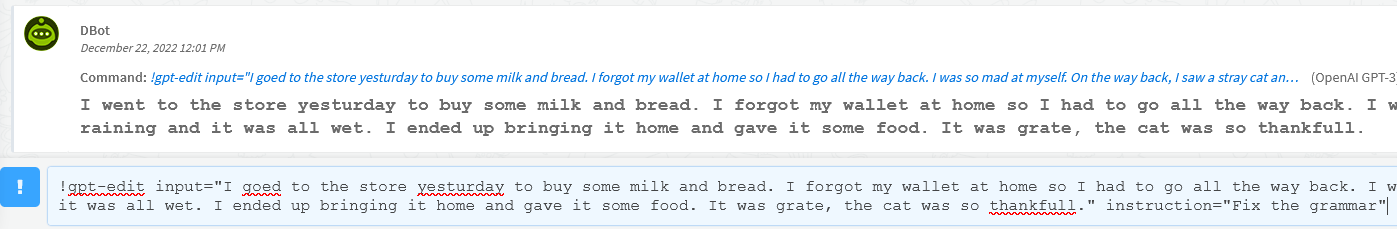
Keep in mind that GPT-3 is effective at interpreting and summarizing language, but does not necessariliy "understand" security paradigms. OpenAI's official stance is that GPT-3 should not be used for security automation and instead should be seen as a tool for dealing with text. In addition, most of the training data for GPT-3 is limited to before 2021. Therefore its knowledge of information or events past 2021 is limited.
Some examples for how GPT-3 can help in Cybersecurity include:
- Analyzing and interpreting security logs: GPT-3 could be used to analyze security logs and extract relevant information, such as extracting all text from a HTTP session.
- Generating reports: GPT-3 could be used to automatically generate reports on security incidents or events, allowing security teams to quickly communicate.
- Responding to security incidents: GPT-3 could be used to automatically respond to security incidents, such as informing stakeholders of the current state of the incident or notifying impacted users.
